 Image Courtesy:commons.wikimedia.org
Image Courtesy:commons.wikimedia.org
A Concerned Indian
As the saying goes, politics is indeed a dirty game. Political espionage has been in existence for several decades now. However, technological innovations and advancements, widespread use of communication devices like cell phones, and the social media reign have seen new propaganda campaign methods emerge. The modern political espionage scenario is plagued with fake news reporting, cyberattack incidents, manipulative ads, and digital content the authenticity of which is hard to verify. Research done by Oxford Internet Institute found that computational propaganda has increased massively and has become prevalent in nearly half the countries.
While political espionage has become widespread, it is capable of disrupting an election. More often than not, mobile espionage is the primary method used to conduct political manipulation, blackmail, and electoral interference. In response, most countries prioritise identifying and preventing threats that may impact election integrity through interference but obviously forget to consider the mobile security of various political candidates, their staff, political consultants, and journalists. Privacy – like eating and breathing – is one of life’s basic requirements. Information is the oxygen of the modern age.
NSO Group Technologies (NSO standing for Niv, Shalev and Omri, the names of the company’s founders) (https://www.nsogroup.com), founded in 2010 is an Israeli technology firm whose military grade spyware called Pegasus enables the remote surveillance of smartphones. The Pegasus spyware is classified as a weapon by Israel and any export of the technology must be vetted & approved by the Defence Export Controls Agency (“DECA”) of the Israeli Ministry of defence. This DECA strictly restricts the licensing of some of the products, and conducts its own analysis of potential customers from the human rights perspective.
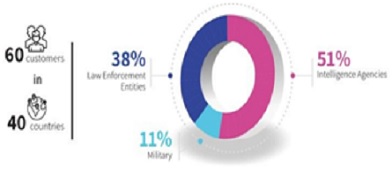
(Source:NSO group Transparency and Responsibility Report-2021)
Modus operandi of Pegasus
As soon as the spyware is installed on a mobile device, it starts getting in touch with the “command and control servers” of the operator. It can then follow instructions and send private data available on the mobile device which includes text messages, event schedules, contacts, passwords, voice calls on messaging apps, location data etc. The spyware also has the potential to turn on the phone camera and microphone, and spy on an individual’s calls and activities.
The targets never heard it. There was no beep, no sound at all. But in those silent seconds, a digital intruder entered their phones. Their private moments and their professional secrets became instantly accessible. Even their cameras could be activated to snap photos at the will, of a faraway attacker. The perpetrators were most likely their own governments. Their tool used to break in was Pegasus, a cutting-edge spyware product made by the Israeli company NSO Group. Through Pegasus, corrupt and troubled regimes across the world can gain access to vast troves of personal information on just about anyone they want. The spyware, sold as a crime-fighting tool, is already known to have been used against journalists, activists, and political dissidents.
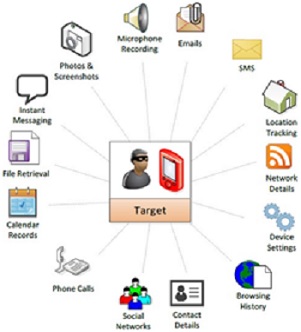
Diagram from purported NSO Group Pegasus documentation showing the range of information gathered from a device infected with Pegasus. Source: Hacking Team Emails.
One of the prominent features of Pegasus is the “Zero Click attacks”. The Zero-Click infection means that the individual is not even required to open a link for them to be attacked with the malware. It gets installed by a missed call or a message even in the most sophisticated high- end android or Apple iPhone. Pegasus has the unique feature of “Zero-Click attacks” to offer which would contain malware links which were specifically designed or custom made for the target. After the installation on a mobile device is complete, Pegasus can use some bypassing techniques in order to read encrypted messages on encrypted messaging apps such as Signal, WhatsApp and Telegram etc. Not only is the method of operation of the spyware scary, its presence on a mobile device is also difficult to ascertain. Murkier is that it self-destructs itself leaving no traces if the infected phone is subject to computer forensics. It can also be used to implant digital material into the computer system which can later be used as evidence in the court of law by the law enforcing agencies.
Although NSO claims that Pegasus is not a mass surveillance technology, it only collects data from the mobile devices of specific individuals, suspected to be involved in serious crime and terror, the scary situation is when the smartphone used as a personal digital diary becomes a spying device invading the bedroom similar to the Big Boss serial watching all its occupants. Political rivals can sponsor hackers to execute an advanced spyware attack exploiting undetected vulnerabilities. This tactic enables them to track phone calls, text messages, activate mobile phone device microphones and cameras at will, track locations, and read text messages. A perusal of NSO’s Transparency Report reads like a sales brochure. It claims to have withdrawn the spyware from five countries. A coincidence that whenever the then Israeli PM visited foreign countries, the sales of Pegasus shot up & whenever any foreign leader visited Israel.
Past Instances of Pegasus being used for spying
There have been several instances of spying using Pegasus reported in the past. For instance, it is claimed that the Saudi Government used it to spy on Jamal Khashoggi before his killing, and in 2019, WhatsApp filed a case against NSO claiming its software was used to attack its users. In July, 2017, Carmen Aristegui who is a Mexican journalist and the founder of the online news outlet Airstegui Noticias, learned that she had been a target of Pegasus.
 Image Courtesy:thewire.in
Image Courtesy:thewire.in
Citizen Lab of the University of Toronto had reported in depth about Pegasus spyware in its Hide and Seek research report #113 in September 2018. They found suspected NSO Pegasus infections associated with 33 of the 36 Pegasus operators identified in 45 countries-India is one among those countries. The findings were based on country-level geolocation of DNS servers, factors such as VPNs and satellite internet teleport locations can introduce inaccuracies as a disclaimer.
The next frontier of electoral verdict interference through smartphone hacking
Cellular technology has evolved by leaps & bounds that today, smartphones can perform similar tasks to a computer. The smartphone is being used like a personal diary. Due to their mobility and effectiveness, the devices are often used in running daily businesses of political contests and campaigns. They are almost indispensable, making them a valuable target for rouge political opponents. The intrusive mobile surveillance tools are readily available to political bigwigs plush with both money and muscle power, the two ‘M’s of electoral politics in the Indian scenario which now has a third ‘M’ added to it which is Mobile phone hacking to influence public opinion. The ill-intended politicians & political parties can use them to suppress dissent & stifle public opinion rendering a democracy to an autocratic or banana republic.
 Image Courtesy:247wallst.com
Image Courtesy:247wallst.com
Politicians can apply similar tactics and hire hackers to infiltrate mobile phones of other political opponents to ‘find dirt,’ such as incriminating communications, pictures, or videos and use them for blackmail or extortion. The main reason why some politicians sponsor hackers to target their opponents’ smartphones is to gain unauthorized access to sensitive information. Political opponents, journalists, and campaign staff use mobile phones as the central points for communications during intensive political campaigns. The devices house a lot of valuable information such as emails, text messages, live images, audio, videos, social media accounts like WhatsApp, Telegram, Facebook, Twitter, Instagram etc. These can be modified to meet the malafide intent, generation of fake & morphed images of the rival political opponents. The opponents with access to such information are more likely to find something to use as a political weapon. Surveillance tools usage is not a new phenomenon since governments and political rivals alike deploy them to discredit their opponents. However, what has changed is the ability to turn a mobile phone device into a spying device to survey every candidate’s move and communication. This can lead into disinformation campaign too which can incite communal passions that can affect an electoral verdict in case of a close contest. These can also be used as blackmail the rivals into submission, force them to cross over to the ruling party causing democratically elected governments to fall or force them to support unfavourable policies, draft draconian laws in parliament. Journalists spend a long time in cultivating their sources in the portals of power. Now with this spyware, this will affect their profession too in fair reporting and bringing the truth in many tricky issues which may help the common citizen.
Pegasus in the Indian scenario
Indian citizens were indeed targets of a vicious, abominable and uncivil surveillance campaign by a government entity, Indian or foreign. The buck stops with the Government of India. Instead of coming clean and explaining what it intends to do to protect citizens, the Government of India has fallen back on a disingenuous claim that no illegal surveillance is possible in India.
 Image Courtesy:commons.wikimedia.org
Image Courtesy:commons.wikimedia.org
Paris based media non-profit organisation Forbidden Stories and human rights group Amnesty International, Organised Crime & Corruption Reporting Project (OCCRP) and 16 other international media partners including The Wire from India around the world worked to uncover who might have fallen victim to Pegasus, and tell their stories under The Pegasus project. The Pegasus project suggests that in India, at least 42 journalists, two union cabinet ministers, civic rights activists, academics, opposition leaders, election strategists, holders of constitutional positions, business persons were possibly subjected to surveillance and hacking. The reports are based on the tranche of a leaked database of about 50,000 phone numbers accessed by the Paris-based non-profit Forbidden Stories and Amnesty International, which they say are numbers of interest to clients of NSO. The database also has the numbers of over 200 journalists worldwide, including Indian media houses such as The Wire, The Hindu, The Indian Express and Hindustan Times. News18, India Today, etc. Even small-town journalists are there in the list. The worldwide list of alleged targets includes at least 180 journalists, 600 politicians, 85 human rights activists and 65 business leaders.
The Wire’s analysis of the data showed that most of the journalists were targeted between 2018 and 2019, in the run-up to the 2019 Lok Sabha elections. NSO refused to make its list of customers public. The presence of Pegasus infections in India, the wide range of persons that may have been selected for targeting, strongly indicate that the agency operating the spyware on Indian numbers is an official Indian one according to the report. Forensic analysis was conducted on the phones of seven journalists, of which five showed traces of a successful infection by Pegasus. It showed that at least ten governments were NSO customers. These countries include Azerbaijan, Bahrain, Kazakhstan, Mexico, Morocco, Rwanda, Saudi Arabia, Hungary, India, and the United Arab Emirates (UAE).
To be sure, the presence of a number in the database does not imply that the person’s device was successfully targeted. Unless evidence is established through a forensic examination, it is impossible to say if there was an attempted or successful hack. Therefore, an important distinction had been made to differentiate the names that appear on the list. A potential target is someone whose number appeared on the list, but whose device had not been forensically analysed by Amnesty. A person is classified as a target if their phones show evidence of an attempted or successful hack. So far, The Wire has revealed the names of 155 people who were targets or potential targets for surveillance by clients of the NSO Group. The Wire has confirmed the numbers of at least 40 journalists who were either targets or potential targets for surveillance. Forensic analysis was conducted on the phones of seven journalists, of which five showed traces of a successful infection by Pegasus. (https://thewire.in/rights/project-pegasus- list-of-names-uncovered-spyware-surveillance).
The explosive revelations include the who’s who of India in various fields –
- journalists-such as MK Venu, Sushant Singh, Siddharth Vardarajan, Vijaita Singh,
- politicians, political figures or individuals linked to them – Rahul Gandhi during the run up to 2019 elections and his aides Sachin Rao, Alankar Sawai, Prashant Kishor (his phone showed signs of successful hack when forensically analysed),
- Abhishek Banerjee,
- present union ministers Ashwini Vaishnaw, Prahlad Singh Patel-his wife, cook, assistants, gardener,
- personal secretary to Vasundhara Raje Scindia,
- officer on special duty (OSD) for Smriti Irani,
- Vishwa Hindu Parishad (VHP) leader Pravin Togadia and others.
 Image Courtesy:usa.kaspersky.com
Image Courtesy:usa.kaspersky.com
They were among the 300 verified Indian numbers listed as potential targets for surveillance during 2017-2019 reported The Wire. Besides, phone numbers belonging to the Supreme Court staffer who accused former Chief Justice of India (CJI) Ranjan Gogoi of sexual harassment in April 2019 also found place in the list of potential snoop targets. In the run up to the toppling of the Congress-JDS government in Karnataka in July 2019, the phone numbers of then Deputy Chief Minister G. Parameshwara, security personnel of former PM Deve Gowda, the personal secretaries of then Chief Minister H.D. Kumaraswamy and former Chief Minister Siddaramaiah were selected as possible targets for surveillance. The Wire reviewed the records of the numbers that were of interest to an Indian client of Israel’s NSO Group. The records indicate that the phone numbers of some of the key political players in Karnataka appear to have been selected around the time when an intense power struggle was taking place between the BJP and JDS-Congress government in 2019, after 17 legislators belonging to the ruling alliance abruptly resigned to force a trust vote in the state Assembly. The list also includes Ashok Lavasa-a potential target when he was election commissioner.
The activists, lawyers and academicians whose phone numbers appear in the leaked records include Ambedkarite activist Ashok Bharti; former Jawaharlal Nehru University students Umar Khalid, Anirban Bhattacharya and Banjyotsna Lahiri; academic and chronicler of life in Naxal- dominated regions, Bela Bhatia; railway union leader Shiv Gopal Mishra; anti-coal mining activist Alok Shukla; Delhi University professor Saroj Giri; Bastar-based peace activist Shubhranshu Choudhary and Bihar-based activist Ipsa Shatakshi, Two prominent political personalities from Assam — Samujjal Bhattacharya from AASU (All Assam Students’ Union) and Anup Chetia from the pro-talks’ faction of ULFA (United Liberation Front of Asom), Naga leaders -Atem Vashum, Apam Muivah, Anthony Shimray and Phunthing Shimrang. The potential targets include industrialists Anil Ambani and a senior official of ADA Group-AN Sethuraman, and their numbers were listed during the time when the Rafale controversy was in full swing and a legal challenge in the Supreme Court. Both Indian and French, had started asking serious questions about Dassault Aviation’s offset partners in India. Even former French President Francois Hollande’s remarks on how one particular corporate partner was chosen had stirred up a storm. Naresh Goyal, Ajay Singh, Prashant Ruia to name a few more businesspersons. Scientists or in the health sector-Dr.Gagandeep Kang, India’s foremost virologists who was involved in the fight against Nipah Virus, Hari Menon of Bill & Melinda Gates foundation.
Eight phones of the then CBI director Alok Verma and his family members were put in the list of devices targeted for snooping soon after he was divested of the coveted charge on October 23, 2018. Along with Verma, phones of his second-in-command Special Director Rakesh Asthana, against whom he had registered a corruption case on October 21, 2018, and the then Joint Director A K Sharma were also put on the list for surveillance using this sophisticated malware. More than 25 people from the Kashmir Valley were identified as potential targets of intrusive surveillance between 2017 and mid-2019. Of these, The Wire was able to conduct forensic analysis on the phones of two– separatist leader Bilal Lone and the late S.A.R. Geelani, who worked as a lecturer in Delhi University and died in 2018. In addition, at least four members of Kashmir’s most influential separatist leader Syed Ali Shah Geelani’s family including his son-in-law, journalist Iftikhar Gilani and his son, scientist Syed Naseem Geelani- were of consistent interest to the Indian client of the NSO group between 2017 and 2019. The leak also shows that the current head of the Hurriyat conference Mirwaiz Umar Farooq was a potential target of surveillance between 2017 and 2019.
National security figures-KK Sharma who was head of BSF, Jagadish Maithani Inspector General of BSF integral to smart fencing project, Jitendra Ojha a senior official from the
Research & Analysis Wing (RAW) to name a few. Bureaucrats, officials from investigating agencies- Rajeshwar Singh-senior ED officer handling important investigations, his sister Abha Singh a noted lawyer, VK Jain-a former IAS officer-who worked as personal assistant to Delhi CM Arvind Kejriwal. Tamil politicians & activists -Seeman of Naam Tamizhar Katchi, Thirumurugan Gandhi-May 17 movement founder, K. Ramakrishnan & Kumaresan.
Surveillance in India appears to be systematic. In 2019, similar allegations were made about the use of Pegasus against journalists and human rights activists. Most of them were situated in Maharashtra and Chhattisgarh as the hack targeted lawyers related to the Bhima Koregaon case and Dalit activists, respectively. However, despite repeated calls for investigations, the relevant State governments failed to do so. WhatsApp’s 2019 discovery that NSO Group spyware had exploited its app revealed that at least 121 Indians had been targeted, including activists who were later imprisoned. More than 2,000 Indian phone numbers appeared on the leaked Pegasus list, indicating that they were potential targets of the software. They include hundreds of journalists, sitting ministers, human rights activists and academics, as well as diplomats from neighboring countries. Of these, 300 numbers have been verified; 22 phones were subjected to forensic analysis by Amnesty International and peer reviewed by University of Toronto’s Citizen Lab. Of these, 10 were clearly established as being targeted by Pegasus; eight of the other 12 yielded inconclusive results. The evidence is strong, and the credibility of these revelations is extremely high.
These revelations highlight a disturbing trend with regard to the use of hacking software against dissidents and adversaries. If it is unauthorized, then it is all the more sensitive as the constitution & rule of law has been trampled compromising the oath of office & secrecy of the union cabinet & national security. Till now, the government has neither confirmed nor denied that it obtained Pegasus spyware.
Image Courtesy:commons.wikimedia.org
Laws applicable at present to surveillance & hacking in India
There are legal provisions for intercepting communication and accessing digitally stored information in the interests of national security and public safety. Even without the use of Pegasus or any other hacking software and surveillance, these provisions are problematic and offer the government total opacity in respect of its interception and monitoring activities. While the provisions of the Indian Telegraph Act relate to telephone conversations, the IT Act relates to all communications undertaken using a computer resource. Currently, the laws authorising interception and monitoring of communications are Section 92 of the CrPC (for call records, etc), Section 5(2) of The Indian Telegraph Act, 1885, states that the government can intercept a “message or class of messages” when it is “in the interests of the sovereignty and integrity of India, the security of the State, friendly relations with foreign states or public order or for preventing incitement to the commission of an offence”.
The operational process and procedures for it appear in Rule 419A of the Indian Telegraph Rules, 1951. Rule 419A was added to the Telegraph Rules in 2007 after the verdict in the People’s Union for Civil Liberties (PUCL) vs Union of India case in 1996, in which the Supreme Court said telephonic conversations are covered by the right to privacy, which can be breached only if there are established procedures. Under Rule 419A, surveillance needs the sanction of the Home Secretary at the Central or State level, but in “unavoidable circumstance” can be cleared by a Joint Secretary or officers above, if they have the Home Secretary’s authorization. Section 92 of the CrPC (for call records, etc.)
The second legislation enabling surveillance is Section 69 of the Information Technology Act, 2000, which deals with electronic surveillance. It facilitates government “interception or monitoring or decryption of any information through any computer resource” if it is in the interest of the “sovereignty or integrity of India, defence of India, security of the State, friendly relations with foreign States or public order” or for preventing or investigating any cognizable offence. The procedure for electronic surveillance as authorised by Section 69 is detailed in the Information Technology (Procedure and Safeguards for Interception, Monitoring and Decryption of Information) Rules, 2009. According to legal luminaries, these rules are very broad and allow even the redirection of traffic to false websites or the planting of any device to acquire any information. Section 69 of the IT Act and the Interception Rules of 2009 are even more opaque than the Telegraph Act, and offer even weaker protections to the surveilled. No provision, however, allows the government to hack the phones of any individual since hacking of computer resources, including mobile phones and apps, is a criminal offence under the IT Act.
Section 66 prescribes punishment to anyone who gains unauthorized access to computers and “downloads, copies or extracts any data”, or “introduces or causes to be introduced any computer contaminant or computer virus,” as laid down in Section 43. Hence, in the present scenario, the use of Pegasus is illegal as it constitutes unauthorized access under Section 66 of the Information Technology Act. Nonetheless, surveillance itself, whether under a provision of law or without it, is a gross violation of the fundamental rights of citizens.
In 2014, the Ministry of Home Affairs told Parliament that nine central agencies and the DGPs of all States and Delhi were empowered to conduct interception under the Indian Telegraph Act. In 2018, nine central agencies and one State agency were authorised to conduct intercepts under Section 69 of the IT Act. Yet, the Intelligence Organisations Act, which restricts the civil liberties of intelligence agency employees, only lists four agencies, while the RTI Act lists 22 agencies as “intelligence and security organisations established by the central government” that are exempt from the RTI Act. It is unclear which entities count as intelligence and security agencies. The breadth of the potential targets in India raises many legal questions. Although the government has the power to surveil, monitor & decrypt communications, hacking is a crime in India.
Thus, the people whose phones have been hacked by Pegasus have an imposing roadblock. How will they or their lawyers challenge the legality of a tool that the government has never acknowledged using? This is a major challenge.
Data protection & privacy laws in India
The cohort of people who were potential targets journalists, politicians, probably a Supreme Court judge and a former Election Commissioner does not indicate that the surveillance was necessitated by national security or public safety concerns. On the contrary, the composition suggests that private craving, turpitude and even voyeurism motivated the perpetrators. This violation is about privacy and much more.
 Image Courtesy:theunfilteredjournal.com
Image Courtesy:theunfilteredjournal.com
Privacy and free speech are what enable good reporting. They protect journalists against threats of private and governmental reprisals against legitimate reporting. This has been recognized in Supreme Court decisions. In the absence of privacy, the safety of journalists, especially those whose work criticizes the government, and the personal safety of their sources is jeopardised. Such a lack of privacy, therefore, creates an aura of distrust around these journalists and effectively buries their credibility.
Information obtained illegally may have been used to compromise institutions, to steal elections, sabotage Opposition campaigns, and even dislodge an Opposition government. That the accused in the Bhima Koregaon case had their computers breached by unknown entities to plant evidence that the prosecution is now using against them is notable in this context.
The law enforcement agencies can trample upon the lives of citizens in such manner while elected representatives plead ignorance is unsettling for a democracy. This is antithetical to the basic creed of democracy. In the K.S. Puttaswamy vs Union of India verdict of 2017, the Supreme Court further reiterated the need for oversight of surveillance, stating that it should be legally valid and serve a legitimate aim of the government. The court also said the means adopted should be proportional to the need for surveillance, and there should be procedures to check any abuse of surveillance. This made it clear that any invasion of privacy could only be justified if it satisfied three tests: first, the restriction must be by law; second, it must be necessary (only if other means are not available) and proportionate (only as much as needed); and third, it must promote a legitimate state interest (e.g., national security).
The Justice Srikrishna Committee on data protection noted that most of India’s intelligence agencies are “potentially unconstitutional”, since they are not constituted under a statute passed by Parliament – the National Intelligence Agency being an exception. The Personal Data protection & privacy bill 2019 is pending before parliament since 2019.
Way forward
Who is ensuring that the surveillance is necessary and proportionate? has any Indian agency bought Pegasus? Did the government acquire the Pegasus spyware? How much did it cost & in which year? Has the government issued notice to Pegasus when a leak was earlier reported in 2019? Why is the government silent? How many licenses were procured?
The truth about these revelations can be unearthed through an investigation by the Supreme Court monitored probe suo moto or any other credible mechanism. The West Bengal government has formed a two-member panel comprising retired judges to probe into the allegations of snooping with the help of Pegasus. The commission will comprise retired Supreme Court judge Justice Madan Bhimrao Lokur and retired Chief Justice of Calcutta High Court, Justice Jyotirmay Bhattacharya. Expressing shock over media reports on widespread surveillance on journalists and politicians using Pegasus spyware, the Editors Guild of India demanded an independent Supreme Court-monitored inquiry into the alleged snooping.
In the USA, after the Watergate scandal, the legacy of the Church Committee could be seen that the Snowden revelations in 2013 did not uncover any spying on Opposition politicians, journalists, judges, and human rights defenders for partisan political ends. What was shocking about the Snowden revelations was the extent of NSA’s surveillance, the overreach of the powers provided under the PATRIOT Act, as well as the lack of sufficient checks and balances provided by the Foreign Intelligence Surveillance Court. The Snowden revelations led to meaningful reform of that court, and controversial domestic surveillance provisions of the PATRIOT Act expired in 2020.
We need such reforms in India, which are aimed at professionalising intelligence gathering, bringing intelligence agencies under parliamentary oversight, making them non-partisan, and ensuring that civil liberties and rule of law are protected. This is India’s Watergate moment, and the Supreme Court and Parliament should seize it. Intelligence gathering needs to be professionalised, parliamentary oversight introduced, and liberties and law protected. In its 2019 election manifesto, the Indian National Congress, a first for a national political party called for parliamentary oversight of intelligence agencies. Petitions have been filed by senior journalists N.Ram & Sashi Kumar for an independent probe headed by a former or sitting judge into mass surveillance of potential “targets” which are from various sections of the society. An open letter to the Chief Justice of India (CJI) by concerned citizens, women rights activists urged that The Supreme Court must declare a moratorium on the export, sale, transfer and use of Pegasus spyware in India and investigate the snooping scandal.
Edward Snowden had said that it is next to impossible of foiling Pegasus comparing it to a nuclear holocaust. Amnesty International has warned of the devastating impact of the poorly regulated spyware industry on human rights worldwide. According to Agnes Callamard, Amnesty International’s Secretary General “This is a dangerous industry that has operated on the edges of legality for too long, and cannot be allowed to continue”. She also said that we urgently needed greater regulation over the cyber surveillance industry, accountability for human rights violations & abuses & greater oversight over that shadowy industry. Amnesty called for an immediate moratorium on any export, sale, transfer and use of surveillance technology “until there is a human rights-compliant regulatory framework in place.”
If smartphones can be hacked, why not EVMs? Food for thought in the world’s largest democracy.
(The author is a citizen of India, deeply concerned about the state of affairs in the country)